Organizations
Overview
As an Organization Admin, you may create and manage security processes that dictate the requirements needed for your users to access your organization.
Organization Discoverability
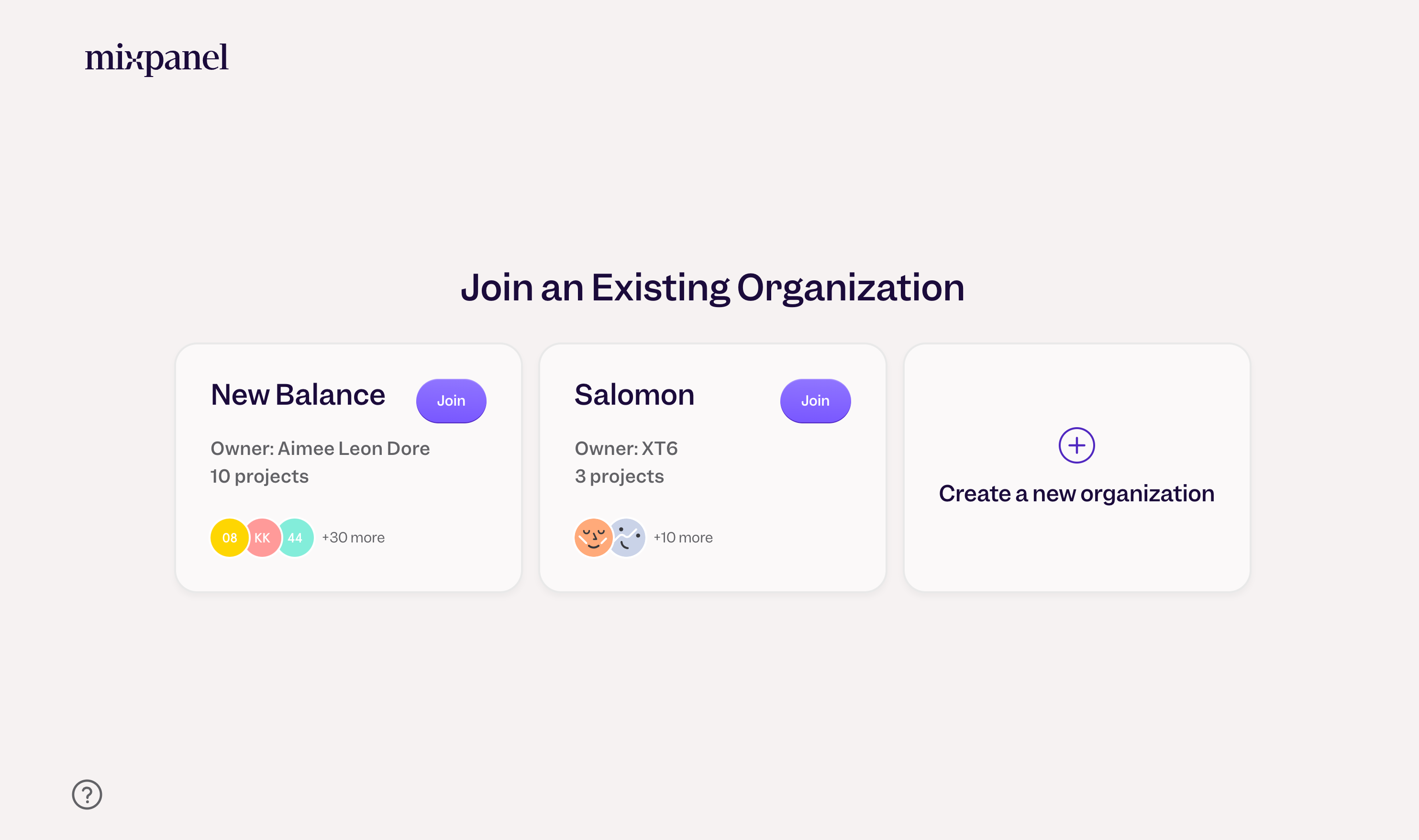
Organization Discoverability makes it seamless for new users with a shared work email domain to connect with teammates in an existing organization in Mixpanel, allowing them to access their team’s projects, data, and reports, instead of joining a new, empty org.
This feature is accessible to new users who have verified their email as well as existing organizations that are on an Enterprise plan and do not have SSO enabled.
Setting Discoverability
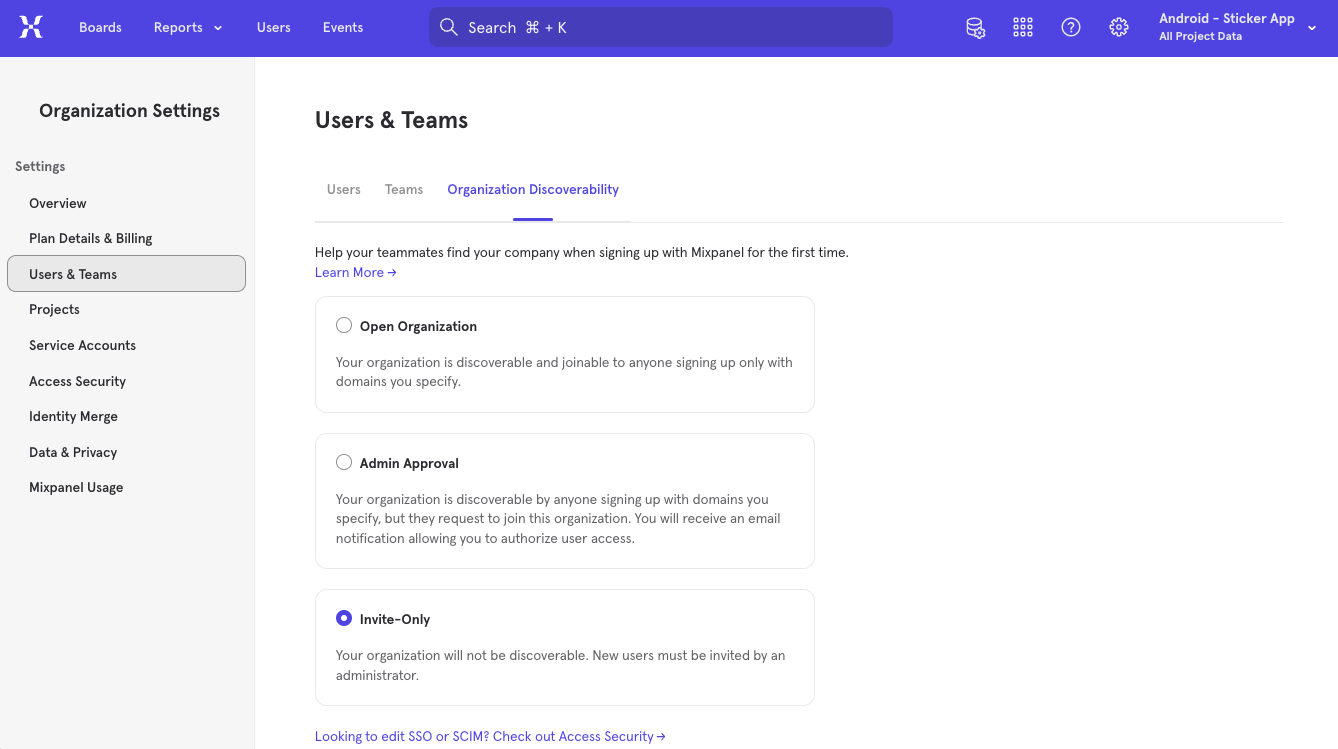
Only organization owners and billing admins can access Organization Discoverability by going to Organization Settings > Users & Teams > Organization Discoverability.
They can enable Organization Discoverability by first specifying the private (i.e. work) email domain(s) that should be granted access when a new user signs up for Mixpanel. Please note that public email domains, such as Gmail or Yahoo, cannot be used.
The org owner or admin can then designate the level of discoverability of their organization; open to join, subject to admin approval, or invite only.
Open Organization: An organization designated “open to join” is discoverable and joinable to any new users with an admin-specified email domain(s).
Admin Approval: An organization designated as requiring “admin approval” is discoverable to any new user signing up with a specified email domain, but can only be joined upon request. Admins will receive an email notification to authorize access.
Invite Only: An organization designated “invite only” is undiscoverable regardless of email domain. New users must be invited by the admin.
Was this page useful?